9 Keys to Successful Third Party Risk Management
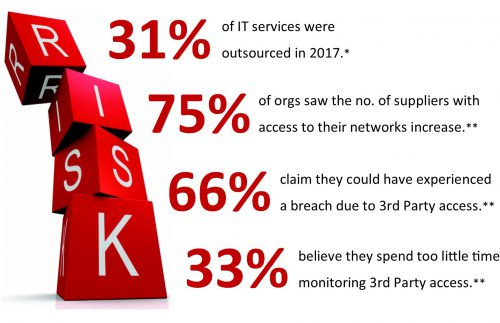
With risks from IT outsourcing increasing and well publicised regulatory pressure and penalties – such as those posed by GDPR and PCI DSS – it has never been more important to evaluate and mitigate risks from the data supply chain and downstream data processors.
Whether you’re at the start of defining a TPRM program or looking to improve your current TPRM processes and procedures, there are 9 key areas any business should address to ensure efficient and effective supplier due diligence.
* Deloitte Tech Trends 2017
** Bomgar 2018 Privileged Access Threat Report
1. Clearly define your program parameters
Don’t forget the 7 P’s of Performance! Define clear objectives and operational goals for your program. Be clear on your business’s risk appetite and agreed decision making criteria when it comes to how you’ll respond to risks you identify.
2. Identify, then classify, ALL your Third Party suppliers
If you can’t measure it, you can’t improve it – so you’ll need to create a definitive list of Third Parties your business engages with, what services they offer and what SLA’s and contractual obligations have been set. Armed with this data, you’ll be able to classify and prioritise Third Parties and the risk treatments you’ll apply.
3. Standardise your assessments and processes
Many businesses develop bespoke risk assessment questionnaires and base them upon management standards such as ISO 27001. However, these frameworks are typically not designed to specifically address Third Party risk. Emerging global standards in TPRM such as Shared Assessments’ Standardised Information Gathering (SIG) questionnaire sets are a great resource to reference.
4. Automate and simplify for all
Automated assessment, analysis and reporting is transforming archaic, manual “email and spreadsheet” processes into streamlined end-to-end workflows. Time freed from data collection and processing can be spent on the more critical risk mitigation and remediation planning. Simplified assessment processes also improve the rates and speed of completion from suppliers.
5. Trust but Verify
Attestations from questionnaire-based assessments should always be corroborated by supporting evidence and documentation. However, suppliers of critical services and those whose risk rating falls below acceptable levels should also be subject to a more rigorous review and verification of their controls and procedures, evidenced in-situ via onsite risk assessments.
6. Continuously monitor risk between assessments
Continuous Monitoring is now becoming a critical element of third-party risk programs with the most comprehensive services cover multiple risk domains including data, operational, financial, brand and regulatory risk. This ensures you are looking beyond tactical network security and gaining the strategic business view that drives a suppliers’ cybersecurity risk. (e.g. investments, divestitures, personnel changes, legal actions, patents etc.)
7. Remember your downstream suppliers
Many IT suppliers outsource their data processing, software development or platform support to Fourth and even Fifth Parties who may represent additional layers of risk. You should look to build accountability throughout the data supply chain within contractual terms and SLA’s as well as adding subcontractor requirements into procurement and RFQ processes. Continuous Monitoring can also offer a primary source of threat intelligence in downstream suppliers.
8. Collaborate and build stronger peer networks
Many industries have a common pool of third parties and suppliers who support numerous (often a substantial percentage) clients. That’s where ‘shared evidence networks’ are becoming more commonplace. These networks centralise storage and sharing of risk assessments amongst members, greatly reducing the effort required to collect and complete surveys for all parties concerned.
9. Report and illustrate the value-add
Reports and dashboards should deliver the right information, to the right people, in the right format and clearly illustrate where the Third Party risk management program is having an impact. Whether that is highlighting improvements in risk and security posture or ROI metrics that engage stakeholders and ensure the ongoing buy-in and understanding of the added value the program is creating.
As with any program of work, Third Party Risk Management is a cyclical process – so you should always find yourself back at Step 1, reviewing your program and ensuring it is fit for purpose. A regular and scheduled appraisal of the program’s parameters, objectives, risk ratings and appetite with key stakeholders will ensure it matures in line with current business strategy.
You’re only as strong as your weakest link
DVV Solutions are here to help. We have developed a suite of managed services and automation tools that improve your ability to manage the increasing volumes and complexity of Third Party supplier risk.
Let us help you take the pain out of Third Party Risk Management. For advice and information:
Call Us: +44 (0) 161 476 8700
Contact Us: Complete our Contact Form
Learn more about our Third Party Risk Management Services and Solutions