Best Practices for Reducing Third Party Risk
The simple truth is that the security measures organisations put in place are not enough to protect them from threats of Third Party risk.
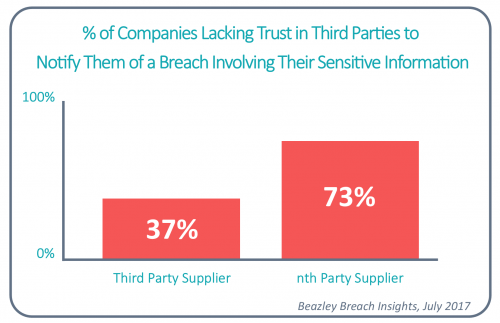
Third Parties can present the greatest area of risk exposure — both for data security and for regulatory compliance. It is much easier for hackers to penetrate smaller Third Party suppliers to get to larger business partners with more robust controls.
As organisations increasingly outsource non-core business processes customer and proprietary data moves beyond their direct control, along with access to critical systems — moves beyond their direct control. Once you are no longer directly responsible for controlling all access to systems and those who touch your data, you lose visibility into all of the places it can go. This has a spider web effect; companies who outsource often discover that the supplier they’re outsourcing to plans to outsource as well.
Knowing the Risks
No t knowing where your data is doesn’t just pose security problems, it has potential regulatory impact. Regulatory pressure around data protection and data privacy is increasing, and the ramifications of
t knowing where your data is doesn’t just pose security problems, it has potential regulatory impact. Regulatory pressure around data protection and data privacy is increasing, and the ramifications of
non-compliance broaden significantly when you think about all of the Third Parties that are essential to your daily operations.
The advantages of the cloud — having data go wherever it can effectively be managed and used at the time — also creates problems. There may be substantive regulatory impacts when data moves cross-border. Many organisations have to know if their data leaves the U.S., and if their European Union (EU) data leaves the EU. You can’t always assure that with a cloud provider. Supplier termination also poses a problem. When you sever a supplier relationship, it is important to ensure that your data is either returned to you or destroyed. Because of how cloud data is stored, that’s not always possible.
An effective Third Party risk management (TPRM) program is essential not only to compliance efforts, but to your overall security posture.
10 Best Practices for Third Party Risk Success
1 – Invest Time in Foundational Elements
Too often, when companies set out to assess suppliers, they rush into developing a questionnaire and initiate assessments without having created the framework for doing so. It is important that the foundational elements of a successful program — policies, procedures, a comprehensive supplier inventory, and the appropriate way of contracting — are well-established.
In order to do this, the right stakeholders need to be involved. Suppliers are the partners of the business unit and need to be treated accordingly by the group that conducts risk assessments. Suppliers have to be comfortable with the process, understand what has to be done, and help to determine what happens when controls aren’t found to be in place.
2 – Look at it as a Lifecycle
Organisations sometimes develop inaccurate expectations about the scope of third-party risk initiatives. Develop your program to make sure that you address the entire lifecycle of your supplier relationships — from selection, to onboarding, to management to termination — and carefully evaluate the cost and effort involved in each step.
3 – Engage in Supplier Prioritisation
It is critical to have a current supplier list that includes the services they provide, the data they access, and the criticality of their services (from an availability standpoint). Which suppliers you need to assess, and what you need to ask them depends on who they are, and what they do for you.
Supplier risk framing starts by assigning a risk rating to the type of service being provided. Start with the risk that is inherent with outsourcing that function. Consider that risk and the security and data protection requirements that need to be placed on any company that’s going to provide that service. That is the inherent risk calculation that will help to place them in the right risk categories.
4 – Get the Contracting Right
A supplier contract is the playbook that details what you can do throughout the relationship. Alignment and synergy need to exist between the contracting process and the people who understand and can define what the risk requirements need to be for that type of service. Whomever is responsible for the contract (Legal, Procurement etc.) should be aware of the provisions required to address the risks associated with a supplier. All contracts are not equal; suppliers need to be held to different accountability standards based on what they are providing.
5 – Assess Your Third Party Risk Maturity
Evaluating the maturity of your Third Party risk program is essential. One area may be more evolved than another. For example, if you’re in a regulated industry such as financial services, the part of your program that is subject to regulatory requirements needs to be more mature than it would be if you were in an unregulated industry. Assess the maturity of the different pieces of your program and decide which of them need attention.
6 – Look at Reporting from the Top Down
Don’t start the reporting process by trying to figure out what data you need to gather. Start by considering all of the reports you have to deliver and who you need to deliver them to. Then you can easily work backward to determine what data you need. There are two central areas to report on — risk and operational effectiveness.
• What risk is the company subjected to by outsourcing a type of service, by supplier, or by service type?
• How effective is the program? Operational assumptions and program performance metrics can help demonstrate the effectiveness of your program and why you may need more resources to accomplish your goals.
7 – Leverage Automation
Assessing your third parties can be a time-consuming, manual effort. In fact, 40 to 50 percent of the time spent involves the process of sending out questionnaires, getting answers back, and validating supplier responses and documentation.
Automation can free risk assessors from tasks that don’t involve their skill sets and speed the process up. With an automated solution, an individual assessor can easily conduct three to six times as many assessments in a year as they can manually.
8 – Treat Them Like a Partner
Many suppliers get assessed often, have good security in place, and don’t want to go through the process hundreds of times a year. When the supplier you need to assess is providing something that is critical to delivering your own products and services, be sure to treat them like a partner, rather than simply dictating what they’re going to need to do for you. Make sure they understand from the beginning what you’re doing, why you need to do it, and what information you need.
A lot of suppliers put together a strong package of information to share with partners that you can use. Those that don’t have information prepared and object to being assessed may be doing so because they can’t possibly meet requirements; therefore, they should not have been on-boarded in the first place. And when it comes to post-assessment remediation, try to put yourself in the place of the supplier. If they don’t have the necessary controls in place, work with your stakeholder business unit to get them implemented, but be fair and reasonable in the expectations you place on the supplier.
9 – Assess Consistently
Sometimes the desire to move quickly — so that a supplier’s product or service can be delivered and start generating revenue — leads companies to initially conduct one level of assessment and then shift to a more extensive version afterward. The problem with this is that may lead you to take on levels of risk you’re not aware of. Without a comprehensive assessment, you may later discover that they don’t have certain controls in place and cannot meet your requirements.
10 – Monitor External Factors
Supplier assessments provide static, point-in-time perspectives; it is important to also monitor outside the scope of the contract for additional factors that are not part of a normal assessment. Consider the following questions:
• Does the supplier face legal action that could impair their ability to deliver services?
• What is their financial condition?
• Are they involved in breach incidents at locations other than the locations where my work is performed?
• Are they subject to regulatory action (OFAC, FTC, or others)?
• Are their executives subject to SEC investigation?
You’re only as Strong
as your Weakest Link
Outsourcing has clear benefits — from lower costs to increased efficiency and productivity in non-core business processes. But the value Third Parties bring can be eroded by associated risks.
Third Party weaknesses are your weaknesses.
By developing and maintaining an effective Third Party risk management program, you can help ensure that your suppliers have strong controls in place and protect your organisation from fiscal, operational, regulatory and reputational risk.
Welcome to DVV Solutions
Established in 1999, we have become one of the UK’s leading providers in the design, implementation and management of Third Party risk management and IT Security services. From fully managed TPRM-as-a-service to process and workflow automation tools, we have developed a comprehensive suite of solutions to support any organisation’s Third Party Risk Management requirements.
We’d be pleased to hear from you and help find the most cost-effective way to develop, maintain or expand your Third Party risk management efforts.
Call Us: +44 (0) 161 476 8700
Contact Us: Complete our Contact Form, or
Learn more about What We Do
This article was originally written and published by Brad Keller, Senior Director, Third Party Strategy, Prevalent Inc. and is published here with the kind permission of Prevalent Inc.