A few thoughts on Small Supplier Risk Assessments – Every supplier represents a potential security risk to your organisation. Whether it’s a small specialised law firm, a local value added reseller delivering technology and providing services, a consultant dedicated to your industry, or an off shore Web developer, it’s important to understand those risks – and perform Small Supplier Risk Assessments to make the best possible decisions before they touch your infrastructure, your systems, and your data.
Suppliers of all sizes and shapes play an essential role in every business. No matter how vertically integrated your organisation, you simply can’t do it all, especially when it comes to information technology. This said, unless the supplier is a security solutions provider, their core competency is most likely not in the area of information security. Therefore, every supplier you do business with represents some form of cyber risk to your business systems, customer data, intellectual property, and other sensitive information.
YOU’RE ONLY AS STRONG AS YOUR WEAKEST LINK
Your IT security is only as strong as its weakest link, and when suppliers are given access to your systems—which may be required in order for them to do their job—your security is now tied to their security competency and related investment (or lack thereof).
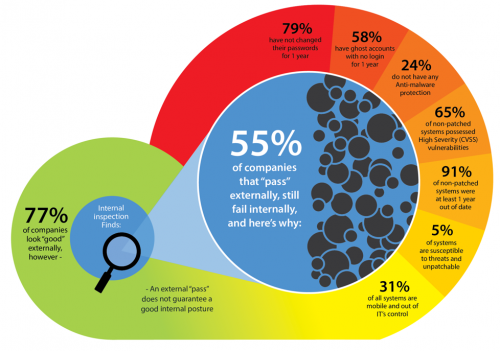
An analysis of Small Supplier Risk Assessments results conducted by DatumSec showed that 55% of suppliers that “pass” an external security audit can have significant internal security flaws that could imperil your own systems – if their email or servers are hacked, will your data, passwords or intellectual property be exposed?
Be aware: not all suppliers are the same in terms of the accessibility of a security assessment. The largest household-names are familiar with being evaluated In this regard. Most do the assessments themselves and keep their security posture as high as possible. Small- and medium-sized companies, however, not so much.
Our focus in this article is dealing with these smaller suppliers – which might be companies that are the right size for your needs, have special knowledge of your specific market segment or technology requirements, offer the best prices for the services rendered, or simply are local to you – but may be lacking in a solid security posture. The question is…do you know? The answer is…you should.
THE THIRD PARTY SUPPLIER RISK LANDSCAPE: MULTIPLE TIERS, MULTIPLE APPROACHES
As business managers, sometimes we work with large suppliers – and sometimes with smaller ones. The biggest Tier-1 household-name suppliers would like to manage everything, but their prices can be astronomical. For many tasks, it makes more sense to work with smaller suppliers who have special competence or provide other benefits tailored to your business. That’s true across the board, from software that you license to services provided onsite by contractors and consultants.
From a security risk assessment perspective, Tier-2, Tier-3, and Tier-4 suppliers are more of a challenge given the fact that these lower-tier suppliers typically have less bandwidth and fewer resources than their larger peers. To be more specific, Tier-3 and Tier-4 suppliers represent most of the risk, since – let’s also be direct – these suppliers are often more concerned about making payroll than maintaining a top-shelf security posture.
FOR SMALLER SUPPLIER RISK ASSESSMENTS, CHOOSE A STAGED APPROACH
No one size fits all – and no one method of performing a thorough Third Party risk assessment fits all suppliers either. So where to start? We suggest the following flow to determine the suppliers’ “Indicators of Posture”, broken down into two views:
External View
a. Internet Services and Configuration Indicator: Are available services associated with a domain configured securely and are applications up to date?
b. Web App Indicator: How is the supplier website configured?
c. Email Indicator: Is the supplier’s email configured to reduce SPAM, is email hosting provider reputable?
d. Web Services Indicator: If the supplier provides web services, how are they configured
e. Cybersecurity Spend Indicator: Supplier size is used as a proxy and other publically-available data is used to estimate Cybersecurity Spend.
Internal View
a. Self-attestation Indicator: How do they view their digital relationship with you – what protections and policies do they believe they have in place to protect your systems and data?
Keep in mind that some suppliers may not know how to respond, or may respond incorrectly to ensure they get the business.
b. Security Policy Indicator: Validate that the supplier has policies defined for user management, password management, access control, patch management, and endpoint protection
c. Security Implementation Indicator: Validate that the policies are being enforced and that security technologies are properly implemented.
d. Security Confidence Indicator: Validate that the supplier assessed their entire organisation, not just the systems they believe are in good working order.
With these two views, you can then establish a Third Party risk baseline. You should proportionally map out a risk baseline on every supplier in the same way… and then enable them to perform their own Small Supplier Risk Assessments in order to meet that defined baseline.
IT’S YOUR DATA SO IT’S UP TO YOU
Who is responsible for managing Small Supplier Risk Assessments? Ultimately, it’s on you, not on any external auditors, not on industry standards bodies or associations, not on one certification program, and—believe it or not—the supplier is not responsible either. We strongly urge you to take charge and perform a stepped Small Supplier Risk Assessments on every supplier—enterprise, large, medium and small—before signing a contract. Certainly, you should have some visibility into the risk they bring before giving them access to your sensitive data and your critical business systems.
As you can expect, the Third Party self assessments might be quite daunting, especially for a smaller firm that may be unwilling to spend the time and effort to perform these tasks. Again, we advise that you ensure that every supplier is secure. Perhaps you could impress upon the supplier that performing this assessment isn’t necessary only to gain your business, but might also improve their own security at the same time, possibly giving them a competitive advantage which could help them win additional business.
The goal is to improve the overall security posture of all of your suppliers such that your security rises as well. This can only be accomplished through a “trust-but-verify” model where your entire supplier pool is classified and the risky suppliers are assessed both through questionnaires and thorough assessments to validate their security posture.
DVV Solutions can provide the automation, services and reporting to perform Small Supplier Risk Assessments that properly validate and verify the security posture of your smaller Third Party suppliers and mitigate your Third Party risk.
Please note: This article contains excerpts used, with kind permission, from the Prevalent Inc. DatumSec White Paper: Assessing & Mitigating Security Risks from Small & Mid-Sized Suppliers, 2016.