Vendor risk visibility and continuous third-party monitoring remains concerningly low despite heightened awareness of the risk and substantial budget increases to tackle the problem
BlueVoyant today released the findings of its second annual global survey into third-party cyber risk management.
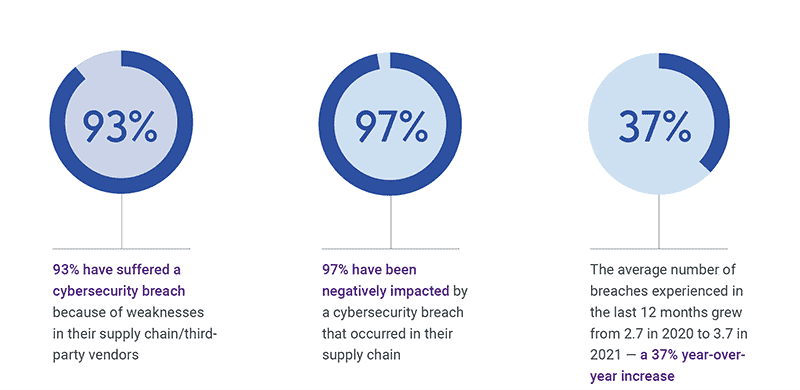
The study reveals that 97% of firms surveyed have been negatively impacted by a cybersecurity breach that occurred in their supply chain. Ninety-three percent admitted that they have suffered a direct cybersecurity breach because of weaknesses in their supply chain and the average number of breaches experienced in the last 12 months grew from 2.7 in 2020 to 3.7 in 2021 – a 37% year-over-year increase.
The study was conducted by independent research organisation, Opinion Matters, and recorded the views and experiences of 1,200 CIOs, CISOs and Chief Procurement Officers in organisations with more than 1,000 employees across a range of industries. It covered six countries: U.S., Canada, Germany, The Netherlands, the United Kingdom, and Singapore.
Key survey findings
- Only 13% of companies said that third-party cyber risk was NOT a priority, a drop compared to last year when 31% of companies said that supply chain and third-party cyber risk was not on their radar.
- 38% of respondents said that they had no way of knowing when or if an issue arises with a third-party supplier’s cybersecurity, compared to 31% last year.
- 91% say that budget for third-party cyber risk management is increasing in 2021, compared to 91% who said this in 2020.
Adam Bixler, Global Head of Third-Party Cyber Risk Management, BlueVoyant, said: “Even though we are seeing rising awareness around the issue, breaches and the resulting negative impact are still staggeringly high, while the prevalence of continuous monitoring remains concerningly low. Third-party cyber risk can only become a strategic priority through clear and frequent briefings to the senior executive team and the board.”
While budgets rise, firms are still experiencing multiple pain points
Reports of the scale of budget increases almost exactly matched figures from last year. Twenty-nine percent of companies reported budget increases from 26-50%; 42% reported increases of 51-100%; and 17% reported increases of 100% or more. Overall, 91% are planning budget increases.
However, the effectiveness of these rising investments is limited by increased adversary attack activity. Surveyed companies report an almost equal distribution of pain points: managing false positives, managing the volume of data, prioritising risk, and knowing their own risk position, among others. The fact that companies are reporting so many issues suggests that larger budgets are not yet resulting in sufficient risk reduction.
Adam Bixler added: “Budget increases demonstrate that firms are recognising the need to invest in cybersecurity and vendor risk management. However, the wide, yet consistent array of pain points suggests that this investment is not as effective as it needs to be. This, tied to the lack of visibility, monitoring and senior-level reporting, underscores a need for further improvement when approaching third-party cyber risk, in order to reduce the exposure of data before attackers take advantage of this.”
Who owns cyber risk management?
Executive ownership was found to be a gray area. According to the survey, 47% of organisations think the CIO owns cyber risk while 38% say it belongs to the CISO, and 11% say chief procurement officers are responsible.
This division over who ultimately owns cyber risk is causing issues around allocation of budget, resources, and ultimately an organisation’s ability to remediate issues when they arise. Some feel it doesn’t matter where risk responsibility falls, so long as it’s at the C-suite level.
Overall, the research findings indicate a situation where the large scale of vendor ecosystems and the fast-changing threat environment is defeating attempts to effectively manage third-party cyber risk in a meaningful way. It is critical for organisations to decide who owns third-party cyber risk.
Until this question is answered, it is impossible to adopt a coherent and effective strategy while developing a meaningful progress to manage it. Third-party cyber risk must be taken out of operational silos and integrated fully with the organisation’s overall risk management strategy with clearly defined lines of responsibility, reporting, and budget ownership.
Without this strategic shift, organisations will remain exposed to unacceptable levels of unmanaged risk and breaches will be the inevitable result.
Variations across industry sectors
Analysis of the responses from different commercial sectors revealed considerable variations in their experiences of third-party cyber risk:
- The business services sector had the highest headcount in its cybersecurity or risk teams and correspondingly were most likely to be monitoring third-party risk daily.
- The healthcare sector exhibited the highest rate of third-party cyber risk awareness and 55% said identifying risk was a key priority, compared to an average of 42%. However, this sector also reported high breach figures, with 29% reporting six to 10 breaches in the last 12 months, compared to a 19% average.
- Manufacturing respondents were least likely to identify supply chain / third-party cybersecurity risk as a key priority and were most likely to be reporting on an annual basis only.
Adam Bixler said: “Our research shows that there are large concentrations of unknown third-party cyber risk across vertical sectors, supply chains and vendors worldwide, and organisations are regularly experiencing vendor-originated breaches. While budgets are rising, the critical question is where funds should be directed to make a tangible impact to reduce third-party cyber risk, helping to close the gaps in visibility, strategy, and monitoring.”
Jim Rosenthal, CEO at BlueVoyant, concluded: “Auditing or sending questionnaires to your supply chain is important, but not sufficient, to stay ahead of agile, persistent attackers. Continuous monitoring and quick action against newly discovered critical vulnerabilities is an essential element for effective third-party risk management.”
Download the Full Report Now
Download Managing Cyber Risk Across the Extended Vendor Ecosystem 2021 to understand the full scope of third-party supply chain cyber risk. Simply register here.
