Aligning Internal Cybersecurity Practices with Third-Party Risk Management
With the recent increase in cyber attacks and new regulations on cybersecurity, you may be wondering how your organisation can bolster its cybersecurity efforts. As the threat landscape grows, so does your organisation’s need to develop a robust, cross-functional cybersecurity program. But where should you start?
To gain comprehensive visibility into your organisation’s vulnerabilities, you need to address cybersecurity internally and externally. ProcessUnity’s latest white paper, developed by cybersecurity and third-party risk management experts, provides best practice guidance for integrating these aspects of your organisation.
Click here to download ProcessUnity’s latest best-practices white paper and build a cybersecurity program that can protect your organisation from all angles. Learn:
- Key Cyber Risk Domains to Identify Internally and Externally: Understand the nuances of compliance risks, operational risks and information security risks throughout your organisation and vendor population.
- Strategic Workflows to Manage Third-Party Cyber Risk: Take a step-by-step look at establishing your cybersecurity controls, mapping your third-party cyber risk and assessing control implementation in your third parties.
- Reporting Tactics for Audits & Program Maturity: Create dynamic reports to track issues over time, prove internal and external compliance and inform project resource allocation.
Kickstart Your Third-Party Risk Management
More often than not, risk, cybersecurity, procurement and supplier management departments are siloed and decentralised, setting themselves up for failure. However, a universal solution that can have dashboards specific to a department’s needs and responsibilities can help to align and streamline the supplier risk management process and manage this complex challenge.
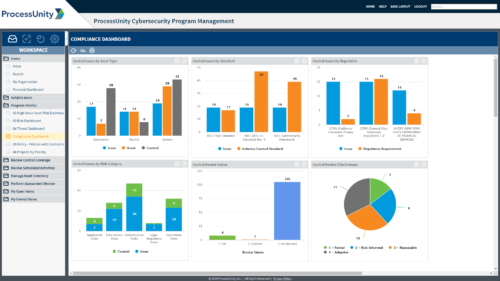
DVV Solutions and ProcessUnity Vendor Risk Management can evaluate, track and measure supplier risk, assess its impact on all aspects of a business and develop compensating controls to lessen the impact if an incident should occur.
For more information on enhancing your cybersecurity oversight:
Call Us: +44 (0) 161 476 8700
Contact Us: Complete our Contact Form, or
Learn more about What We Do
