Late last week, Apache released yet another update to mitigate the Log4j vulnerability and further flaws discovered as the incident has progressed.
The newest update is version 2.17.0, which works to patch a denial of service, or DOS, vulnerability, known as CVE-2021-45105. It is important to update to 2.17.0 immediately, and continue to update with each future release of Apache Log4j versions. Black Kite is working to stay up to date and keep our readers informed as information is released.
The Log4j vulnerability is continuing to make waves as thousands of threat actors take advantage of vulnerable organisations. In fact, hundreds of exploit attempts occur every minute according to the latest research.
Are there any attacks in the wild?
Once an attacker obtains complete access and control of an application, depending on the type of the vulnerability, he can accomplish a variety of goals. Coin miners have been installed, Cobalt Strike was used to facilitate credential theft and lateral movement, and data was exfiltrated from infected systems. Hackers have already started to push malware and ransomware using RCE. Here are some of the most notable exploitations so far:
- Log4j exploited to install Dridex trojan and Meterpreter: Log4j vulnerability is exploited to infect Windows devices with the Dridex Trojan and Linux devices with Meterpreter.
Source (12.20.2021) - Log4j Vulnerability has been adopted by two Linux Botnets: Netlab 360 reports that the threat actors exploit the log4j vulnerability to install the Mirai and Muhstik malware on vulnerable linux devices.
Source (12.11.2021) - New Ransomware group Khonsari: It’s the first ransomware group to begin targeting Log4j.
Source (12.13.2021) - TellYouThePass ransomware: Threat actors have resurrected the TellYouThePass ransomware family, deploying it in attacks against Windows and Linux machines to exploit a severe remote code execution issue in the Log4j.
Source (12.16.2021) - Conti ransomware uses Log4j vulnerability to access VMware vCenter servers.
Source (12.17.2021) - Ten families of malicious samples are spreading using the Log4j2 vulnerability now.
Source (12.13.2021) - Microsoft said nation-state groups from China, Iran, North Korea, and Turkey are now abusing the Log4Shell (CVE-2021-44228) vulnerability to gain access to targeted networks.
Source - StealthLoader Malware Leveraging Log4Shell.
Source (12.15.2021) - Log4j Attack Payloads In The Wild.
Source (12.17.2021)
Across the globe, hundreds of thousands of attempts have been blocked, with the majority happening in the United States and Europe.
One of the latest exploits involved a ransomware known as Khonsari. Hackers used the vulnerability to attack Windows devices with Khonsari ransomware. Using RCE, attackers encrypt the device’s files and in turn ask for ransom by means of Bitcoin.
Since the Log4j vulnerability allows cyber criminals to easily gain control over a device, ransomware just like this, or other harmful activity, may continue to occur as this incident unfolds.
Black Kite built a Log4j platform extension from a trusted online public data set. The vulnerability is being continuously monitored and updated as organisations self-report and external data is released.
How can I see vendors who may be affected by LOG4J vulnerability?
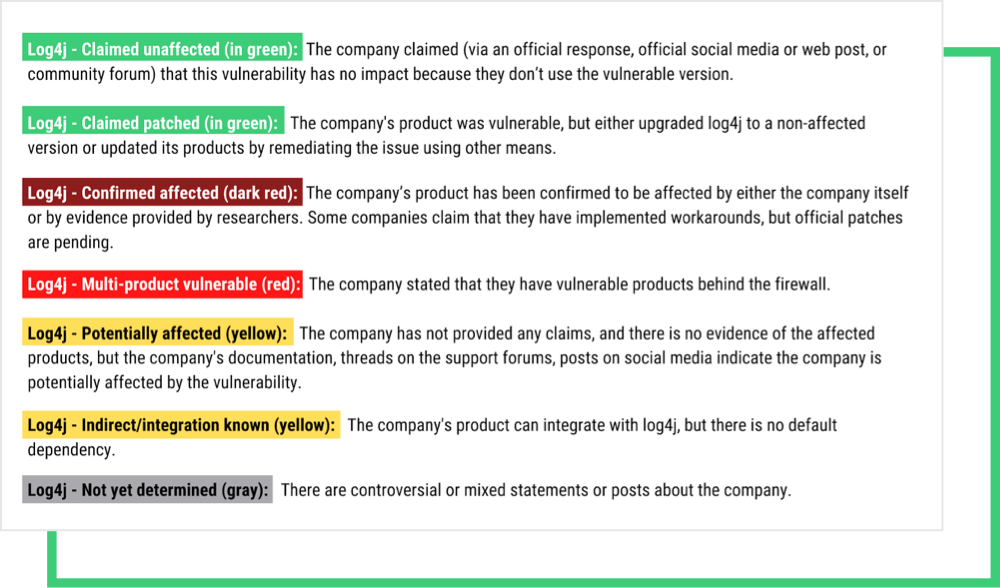
Companies are identified in the Black Kite platform using ‘Tags’ based on their publicly-posted Log4j status (See details below).
PLEASE NOTE: Black Kite does not directly scan or communicate with any publically-facing assets. Open Source Intelligence (OSINT) is used to detect exploits and vulnerabilities.
The Tag definitions are listed below:
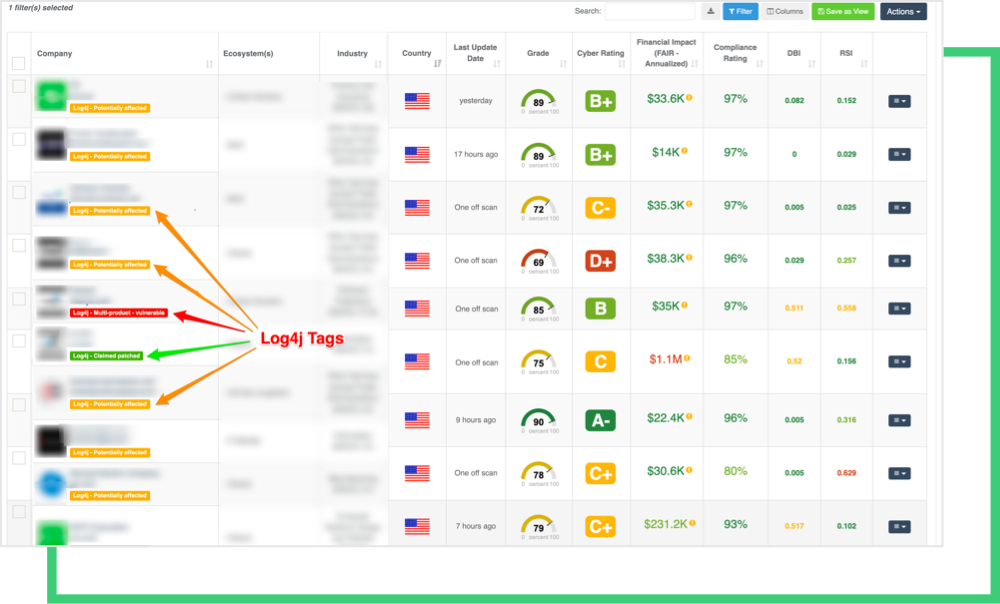
Tags are displayed beneath each company’s profile, as seen below:
To see the vendors with log4j information,
- Go to the Ecosystems > Company List, and click on the Filters button.
- On the pop-up window, click on the Tags field. Select the log4j tags to filter and display.
- Click on the Filter button.
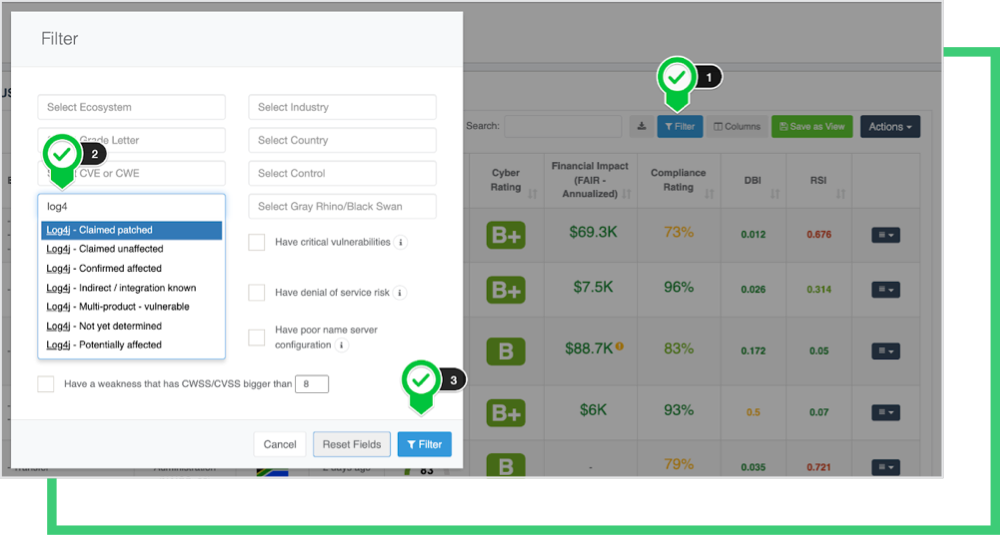
As of now, the new log4j-related information does not affect the grade of the companies.
Attackers perform an HTTPS request against their target system, which generates a log using Log4j that leverages JNDI to perform a request to the attacker-controlled site. The vulnerability will then cause the exploited process to reach out to the site and execute the payload.
Curious to read more? Here is how attackers are thumb printing vulnerable systems.
LOG4J RCE vulnerability, LOG4SHELL, puts millions at risk
A remote code execution vulnerability was discovered in the Apache Log4j 2 Java library on Thursday December 9th, putting any Java-based application or service under extreme active risk. Right this second, threat actors are scanning the internet for vulnerable systems to exploit and gain control of vulnerable systems.
The zero-day vulnerability is dubbed Log4Shell or LogJam, and allows attackers to obtain control of log messages and execute code. This opens the possibility for threat actors to place harmful malware on your server using remote code execution (RCE) if your application is running on the vulnerable version of Log4j.
As we speak, thousands of attempts are being made to exploit this flaw. Over the last few days, new versions of the exploit are being introduced as well, opening up hundreds of alternative ways that attackers can use the vulnerability to their advantage. The latest attacks take aim to install cryptocurrency-mining malware specifically on Microsoft servers that are unpatched by leveraging the Log4j vulnerability.
What is the first step?
You must update your Log4j library now.
If your applications or services use Log4j, you should immediately install and upgrade to the newest version, v. 2.16.0, which patches the original vulnerability, AND the newest discovered vulnerability, tracked as CVE 2021-45046.
How critical is the LOG4J vulnerability?
The Alibaba Security Team first discovered and reported the Log4Shell vulnerability, now tracked as CVE-2021-44228. Apache Software Foundation (ASF) sent an announcement on Saturday and released a new version of Apache Log4J (v. 2.15.0) that patches the vulnerability.
The second and latest vulnerability, CVE 2021-45046, was discovered Tuesday December 14, as the original update was “incomplete in certain non-default configurations.” This prompted the release of newest version of Apache Log4J 2 (v. 2.15.0).
Oracle Security Alert Advisory determines the CVSS (v3.1) score for Log4Shell as 10.0 out of 10.0, indicating high criticality. The vulnerability can be exploited remotely without authentication, meaning threat actors can access it on a network without the requirement of any login data, authentication or credentials.
Once an attacker gains access, they can quickly exfiltrate data or deploy ransomware to the vulnerable system. Since millions of applications and services use this logging system, it makes this risk that much more dangerous.
Additionally, there is no need to write complex code to exploit the vulnerability. Just a single line of code is necessary to start communication between the vulnerable system and the external host.
Similar vulnerabilities have been exploited in the past, resulting in substantial data breaches like the Equifax data breach in 2017. Considering Log4j’s widespread use by many organisations, we can expect similar large data breaches if the vulnerability is not patched immediately.
Who is at risk?
Apache Log4j versions 2.0 to 2.15.0 have the Log4Shell vulnerability.. The library is widely used by many enterprise applications, cloud services, and web applications. Web applications are likely more vulnerable to RCE attacks targeting Log4Shell. Since the majority of Java applications use the Log4j library, organisations could experience a cyber incident even from a non-critical or unexpected application.
According to this GitHub source that provides attack surface information related to the Log4Shell vulnerability, Apple, Tesla, Amazon, and Cloudflare are just a few of the many technology providers affected by the vulnerability. This source also provides screenshots that show evidence for the impacts. At this time, 35 technology manufacturers and components are listed, and 29 are verified.
How do you check for vulnerability?
Different Log4Shell detection systems have been developed since the first release of the PoC exploit. Open-source tools and recommendations are flooding into the cybersecurity community.
For instance, if the following code on the Linux systems provides “binary file matches” as an output, then log4j is used in the relevant system.
grep -r ‘org/apache/logging/log4j/core/lookup/JndiLookup.class’ /
Other code examples found here assist in searching for exploitation attempts.
What is Black Kite doing?
The Black Kite Security Team has been taking immediate steps to detect the Log4j libraries in use and install the newest version to Black Kite environments if detected. We will continue monitoring the exploit attempts toward Black Kite systems and keep an eye on the security logs. We encourage all of our partners and customers to do the same. The high exploitability of this vulnerability on a widely-used library has the potential to cause severe damage to your systems, resulting in data breaches or ransomware incidents.
Black Kite is aware of the vulnerability and has completed verification that this issue does not affect Black Kite products or services.
Black Kite and DVV Solutions will continue to provide updates to this service (and this update) as necessary. Last update: 22/12/21
Get Your Free Cyber Risk Rating
See how simple and effective Third-Party Cyber Risk Management can be with DVV Solutions and Black Kite.
Register Now and receive a complimentary Technical, Financial, and Compliance rating of your company or any supplier in your ecosystem.
Or for more information on how DVV Solutions can mature and scale your TPCRM program:
Call Us: +44 (0) 161 476 8700
Contact Us: Complete our Contact Form, or
Learn more about What We Do
About Black Kite
Black Kite redefines vendor risk management with the world’s first global third-party cyber risk monitoring platform, built from a hacker’s perspective. With 300+ customers across the globe and counting, we’re committed to improving the health and safety of the entire planet’s cyber ecosystem with the industry’s most accurate and comprehensive cyber intelligence.
While other security ratings service (SRS) providers try to narrow the scope, Black Kite provides the only standards-based cyber risk assessments that analyse your supply chain’s cybersecurity posture from three critical dimensions together: technical, financial, and compliance.