 NIST released two industry standards to drive security requirements around supply-chain (a.k.a Third-Party) management. Here’s an overview of the NIST guidelines regarding continuous Third-Party risk monitoring.
NIST released two industry standards to drive security requirements around supply-chain (a.k.a Third-Party) management. Here’s an overview of the NIST guidelines regarding continuous Third-Party risk monitoring.
NIST 800-53
NIST 800-53 Security and Privacy Controls for Federal Information Systems and Organisations sets out guidelines and controls for protecting the government’s sensitive information as well as citizens’ personal information from information security and cyber attacks. It aims to help federal agencies and contractors meet the requirements set by the Federal Information Security Management Act (FISMA).
The controls (operational, technical, and management safeguards ) and guidelines are evolving in accordance with changes in the information and cyber security landscape as well as shifts in infrastructures, and business models. However, the ultimate goal remains the same: To maintain the integrity, confidentiality, and security of federal information systems.
Currently, the draft publication is released for the fifth revision. Some important changes in this revision are:
- Integrating privacy controls into the control set,
- Scoping controls to be used by different interest groups such as systems, engineers, software developers, enterprise architects; and mission/business owners;
- Integration with different risk management and cybersecurity approaches such as NIST Cyber Security Framework,
- Incorporating new controls based on threat intelligence
How NIST 800-53 Views Third-Parties
NIST views supply chain risk management as a critical organisational function. Organisational assets need to be protected throughout the system development life cycle. A standardised process need to be addressed with respect to supply-chain risk of information systems and system components. Another important process is to educate the acquisition workforce on threats, risk, and required security controls.
Most of the supply-chain related controls are listed under System and Services Acquisition Policy and Procedures of NIST 800-53 and in particular SA-12 controls.
Organisations can leverage these controls;
- to reduce the likelihood of unauthorised modifications at each stage in the supply chain; and
- to protect information systems and information-system components, prior to taking delivery of such systems/components.
NIST Supply-Chain Risk Management in a Nutshell
- Employ organisation-defined tailored acquisition strategies, for the purchase of the information system and/or system component
- Conduct a supplier review prior to entering into a contractual agreement
- Employ security safeguards to limit harm from potential adversaries
- Conduct an assessment of the information system, system component, or information system service prior to selection, acceptance, or update.
- Use all-source intelligence analysis (inc. OSINT) of suppliers and potential suppliers of the information system
- Employ at least one of those: organisational analysis, independent Third-Party analysis, organisational penetration testing, independent Third-Party penetration testing
NIST Cyber Security Framework (CSF)
 In April 2018, NIST updated its cybersecurity framework, clarifying and enhancing some of its requirements. An important part of the update is on expanding the Cyber Supply-Chain Risk Management process and additional section Buying Decision.
In April 2018, NIST updated its cybersecurity framework, clarifying and enhancing some of its requirements. An important part of the update is on expanding the Cyber Supply-Chain Risk Management process and additional section Buying Decision.
This framework can be seen as a common language aiming to improve “risk and cybersecurity communications” both internally, a.k.a. from server room to the board room, and across stakeholders. It is an inclusive framework that can be used across many businesses and different domains.
The framework simplifies the cybersecurity functionalities within an organisation by narrowing down to five functionalities; Identify, Protect, Detect, Respond, and Recover, following similar steps to that of NIST SP 800-53.
Section 3.3, Communicating Cybersecurity Requirements with Stakeholders, explains how to use the framework to manage supply chain risk.
Cyber SCRM addresses both the cybersecurity effect an organisation has on external parties and the cybersecurity effect external parties have on an organisation. Organisations can communicate through the Current Profile or Target Profile to express its cybersecurity state/requirements either with their existing or prospective suppliers.
Most of the supplier-related actions are contained in the Identify (Supply-Chain Risk Management) Functionality of the framework.
Cyber SCRM activities may include:
- Determining cybersecurity requirements for suppliers,
- Enacting cybersecurity requirements through a formal agreement (e.g., contracts),
- Communicating to suppliers how those cybersecurity requirements will be verified and validated,
- Verifying that cybersecurity requirements are met through a variety of assessment methodologies, and
- Governing and managing the above activities.
How DVV Solutions and NormShield Can Help
Comprehensive Cyber Risk Ratings
NormShield cyber ratings can be directly leveraged in the whole supply-chain risk management process that is covered under SA-12 of NIST 800-53 and Supply Chain Risk Management function of NIST CSF.
Compliance Module
Knowing the cybersecurity maturity level by assessing compliance levels is a key component in reducing Third-Party risks. NormShield’s standards-based approach makes it easy to estimate and assess compliance levels of Third-Parties. NormShield correlates cyber risk findings to industry standards and best practices. The classification allows organisations to measure the compliance level of any company for different regulations and standards including NIST 800-53, ISO27001, PCI-DSS, HIPAA, GDPR, and Shared Assessments.

Probable Financial Impact Rating based on Open FAIR
NormShield uses Open FAIR model to calculate the probable financial impact if a Third-Party vendor, partner or supplier experiences a breach.
It communicates risks in quantitative, easy-to-understand business terms.
Open FAIR has become the only international standard Value at Risk (VaR) model for cybersecurity and operational risk, meeting the criteria of “..implementing a standardised process to address supply chain risk” of NIST 800-53 SA-12.
A Summary of NormShield Features to Utilise
The below table summarises how NormShield can be utilised to understand the compliance level of Third-Parties for NIST control items. 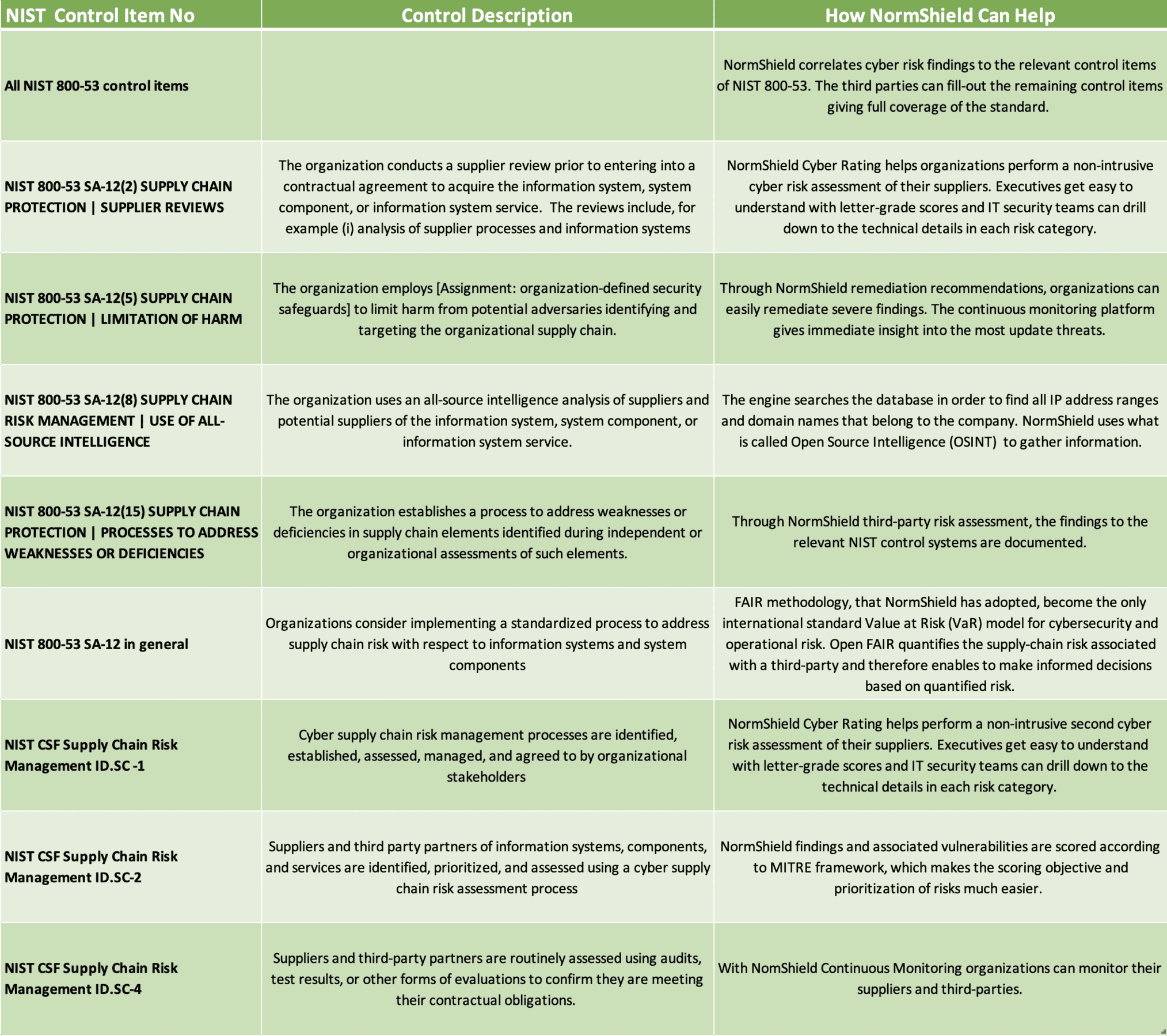
This blog was originally published by NormShield and is shared with their kind permission.
About NormShield
NormShield enables enterprises to monitor their external cyber risk posture and perform non-intrusive cyber risk assessments of their suppliers, subsidiaries and target acquisitions. Using easy-to-understand reports, we provide standards-based letter grades on various risk categories, along with data on how to mitigate each risk in priority order. Learn more at www.normshield.com.