Continuing NormShield’s blog series on third-party cyber risk management, this article’s topic is Cyber Risk. In a digital world, organisations are exposed to a range of risks resulting from cyber events like phishing, data theft, ransomware, corporate espionage, etc… What’s more, these events might happen beyond the company’s knowledge.
Continuing NormShield’s blog series on third-party cyber risk management, this article’s topic is Cyber Risk. In a digital world, organisations are exposed to a range of risks resulting from cyber events like phishing, data theft, ransomware, corporate espionage, etc… What’s more, these events might happen beyond the company’s knowledge.
Within a company ecosystem, the effect of a cyber event quickly multiplies, even extending to several other victims of these intersecting circles. This is what we call Third-Party Cyber Risk.
Starting from the risk terminology, here is what you need to know about cyber risk and how DVV Solutions and NormShield can help with continuous third-party cyber risk monitoring.
What is “Cyber Risk”?
Cyber risk is any risk from the digital world, including damage to the reputation of the company, such as financial loss, operational disruption, data breach, and a negative event affecting the information system. The cyber risk could emerge in a variety of ways such as:
- Breaches of security to gain unauthorised access to information systems.
- Unintentional or accidental breaches of security.
- IT risks due to factors such as poor configuration, poor integrity,
with the most common types being
- Malware,
- Phishing,
- Spear Phishing,
- “Man in the Middle” (MitM) attack,
- Trojans,
- Ransomware,
- Denial of Service attack or Distributed Denial of Service Attack (DDoS),
- Attacks on IoT Devices.
What is Risk in “Cyber Risk”?
According to FAIR Institue, the risk is defined as ”the probable frequency and probable magnitude of future loss” associated with a specific event. In simple terms, one can identify risk as “probable loss” in a predetermined scenario. To accurately define a risk, one needs to talk about a threat scenario, the affected asset(s), their value to the organisation and the possible consequences.
If one of the elements of this tuple is missing we can’t properly talk about risk. In many conversations, even the security professionals misuse the words “risk”, “cyber risk” when referring to an event or a threat. And often, the assets’ value with regards to the company itself and to regulations, sometimes even the assets themselves are ignored in those conversations.
Why terms matter for third-party risk management
It is important that (third party) risk management professionals learn to speak about risk in the same language as it will allow them to focus their limited resources on vendors who present a high probability and/or impact risk beyond the organisation’s risk appetite, instead of performing time-consuming assessments on a vendor who poses a low probability of financial loss if an adverse event were to happen or on vendors who pose a little risk overall.
The Consequences of Unmanaged Cyber Risk
Unmanaged or poorly managed cyber risks can lead up to a variety of cybercrimes, with consequences ranging from data disruption to reputation and eventually to financial loss. If this is happening in a business ecosystem, the effect of a cyber event quickly multiplies, even extending to several other victims creating a ripple effect.
Take the famous Target 2013 breach as an example. Attackers hacked into Target’s network after hacking a third party vendor providing heating, ventilation, and air conditioning services. At the end of the day, the breach affected more than 60M customers across 41 states in the US and exposure of 40M credit/debit card information. Excessive access rights granted to third-party vendors and poor configuration of the system eventually allowed hackers gaining access to the customer service database. Target agreed to compensate up to $10,000 to each customer who proved to have suffered from a breach as a result of the $10 million class-action lawsuits in 2015.
Another famous cyber event creating a ripple effect was the AMCA breach. When AMCA, a bill-collection vendor for several health institutions, was hacked through a web payment portal, the incident affected 17 health institutions including the US biggest lab testing companies, that AMCA provided service for.
Like in the above cases, businesses often find themselves in the middle of a public relations nightmare as they struggle to recover lost assets and prevent further theft.
The digital age has created access to so many things that were never expected. Data breaches are simply the result of exploiting the many vulnerabilities that exist in this digital environment. Assessing the risk and its value is quickly becoming a critical need for many organisations.
So it is time for businesses to start asking this question (if not already asked): If there were a security breach or data loss, what would it cost and how can we mitigate it?
 DVV Solutions & NormShield can help
DVV Solutions & NormShield can help
Monitoring and continuous oversight on your Third-Party vendors and supply-chain are critical. That goes beyond your organisation including anywhere your data is handled during the process.
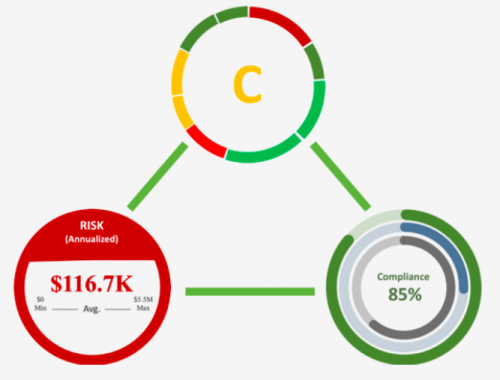
NormShield Third-Party Cyber Risk Assessment continuously assesses an organisation, captures critical information in the cyber risk dashboard and provides detailed drill-down capabilities to fully understand each risk. Ongoing monitoring surfaces priority risks and measures cyber risk posture improvement over time.
By providing Cyber Rating (technical), Compliance Estimations (policies and processes) and FAIR results (the probable impact in financial numbers), NormShield’s vision is to give a complete risk picture of a Third-Party.
Request your Free Rapid Cyber Security Rating here.
Quantify Cyber Risk in Real Financial Terms
Having the capacity to use a FAIR assessment at scale for third-party risk management elevates your risk management program. This tool will help attain the goal of cost-effectively achieving and maintaining an acceptable level of loss exposure, while also clearly conveying the breadth of risk factors across the organisation.
Learn more about the FAIR Model.
This blog was originally published by NormShield and is shared with their kind permission.
About NormShield
NormShield enables enterprises to monitor their external cyber risk posture and perform non-intrusive cyber risk assessments of their suppliers, subsidiaries and target acquisitions. Using easy-to-understand reports, we provide standards-based letter grades on various risk categories, along with data on how to mitigate each risk in priority order. Learn more at www.normshield.com.