Conducting a due diligence process for vendors or third-parties can be cumbersome in today’s digital environment. Unfortunately, these entities are the weakest elements of a digital ecosystem. Regardless of a company’s size or sector, business leaders should take on a rigorous vendor due diligence process, with a proactive defense mindset.

According to IBM’s Cost of Data Breach Report 2020 [1], third parties (a.k.a. vendors) accounted for the largest contributors to a data breach. The study indicates the average total cost of a breach increases by more than $200,000 when a third party is involved.
With a rising trend of third-party induced attacks in the new cyber landscape, let’s understand what third-party due diligence is about and walk through the steps for an effective due diligence process.
WHAT IS THIRD-PARTY DUE DILIGENCE?
To understand third-party due diligence, let’s first take a look at the definition of due diligence:
Due diligence is an in-depth investigation, or analysis carried out to validate the facts of a matter under consideration.
Although the term is heavily used in the finance industry for providing concise financial information to potential buyers, it slightly differs in TPRM and the cybersecurity domain. Third-party due diligence means verifying that third parties or vendors do not pose an intolerable risk to your business.
IT executives must keep their data from malicious actors and strengthen their cybersecurity practices. With cyber risk monitoring, it is important to make sure your vendors treat cybersecurity with the same importance as your organization.
STEP 1 – IDENTIFY THE CRITICALITY OF VENDORS
The very first step of the due diligence process is identifying the criticality of your vendors in your business’ cyber ecosystem(s). Each player in a cyber ecosystem may vary from private firms, non‐profits, and government entities to processes, cyber devices, and even human-beings. It is of utmost importance that third-party risk managers or business owners position their vendors the right way. Decision-making that can be leveraged in identification can include:
Check the type of service vendor provides. It could be as critical as a Software provider or a Hosting provider
Check the type of access granted to the vendor such as Internal VPN access, and
Physical access
Check the number and type of data shared with the vendor, including the number of PII records, type of PII records, and the volume of business-confidential data shared
STEP 2 – LOOK FOR YOUR ASSETS
It is important that business owners take care of their assets, and in particular their data. Whether it be company confidential data such as proprietary manufacturing, engineering process, or the PII of a customer, you need to know where your data extends in the entire ecosystem. NormShield’s third party data breach portal displays numerous breaches over the years caused by cloud vendors, software vendors and even suppliers.
A significant percent of these breaches result from once-shared and then forgotten data on cloud servers and/or vendor servers.
STEP 3 – MAKE VENDORS A PART OF YOUR RISK ASSESSMENT
It is important that risk managers adopt the same risk-aware attitude in the due diligence process. This logic will allow them to focus their limited resources on the vendor issues which present a risk beyond the organization’s risk appetite.
Risk managers should delve into threat scenarios, the shared and affected asset(s), their value to the organization, as well as their value to the entire ecosystem. Threat scenarios and their possible consequences with regards to the contracts and regulations should also be thoroughly analyzed.
STEP 4 – USE A FRAMEWORK TO MAKE STEP 3 MANAGEABLE
The NIST CyberSecurity Framework (CSF) comes handy in the vendor due diligence process. In fact this framework can be seen as a common language aiming to improve “risk and cybersecurity communications” both internally and across stakeholders in a cyber ecosystem.
It is an inclusive framework that can be used across many businesses and different domains. The cybersecurity functionalities are narrowed down to five functionalities here; Identify, Protect, Detect, Respond, and Recover. [2].
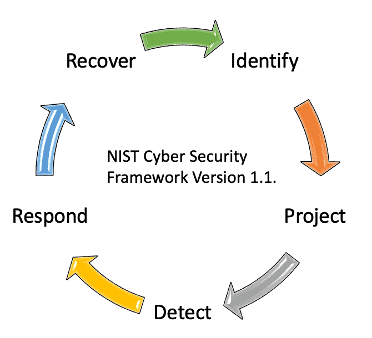
Identify: The Identify Function assists in developing an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities. In the vendor due diligence context this function includes:
- Understanding assets, in particular shared assets
- Identifying cybersecurity policies within the vendor
- Identifying a Risk Management Strategy for the organization including establishing risk tolerance with a perspective of shared services and data
Protect: This function outlines appropriate safeguards to ensure delivery of critical services. Examples include:
- Which protections for Identity Management and Access Control are in place at a vendor
- Data Security protection consistent with the organization’s risk strategy
Detect: The Detect Function enables timely discovery of cybersecurity events. This includes ensuring Anomalies and Events are detected, and their potential impact is understood
Respond: Includes activities once a cybersecurity incident is detected. The Respond Function is about containing the impact of a potential cybersecurity incident. This includes checking to see if any mitigation activities are performed to prevent expansion of a cyber event
Recover: This function includes maintaining plans for resilience and restoring any capabilities or services that were impaired due to a cybersecurity incident. This might include checking to see whether there are improvements based on lessons learned and reviews of existing strategies on the vendor side.
STEP 5 – USE AN ASSESSMENT TOOL
Businesses have been leveraging vendor assessment tools for years, either remotely through vendor questionnaires, surveys or on-site audits. Although vendor questionnaires are still part of the due diligence process, they have proven to create shortcomings over the years. Some of these include:
- vendors might not be fully transparent in the fear that the results will affect the relationship
- questions might not cover all the risks
- the answers will be scoped with third party’s knowledge on the Information Security infrastructure
Relying solely on a questionnaire makes the due diligence process less reliable. Although a more reliable option, on-site audits are very costly and time consuming.
With this in mind, Security Rating Services have brought a new perspective to the vendor risk management and due diligence processes. Organizations have consulted credit rating agencies, like Moody’s, Fitch, and S&P, for years to learn more about their financial posture. In essence, the security grade an SRS assigns to a company is not very different from a credit rating.
A COMBINATION OF CYBER RATING AND COMPLIANCE MODULES IN DUE DILIGENCE
 With the NormShield Compliance Module, the cyber risk rating findings allow you to predict the compliance level of the target company in terms of different regulations including NIST 800-53, NIST 800-171, NIST CSF, ISO27001, PCI-DSS, OTA, HIPAA and GDPR. This process could be a vendor assessment in the due diligence process or a third party in an existing supply-chain.
With the NormShield Compliance Module, the cyber risk rating findings allow you to predict the compliance level of the target company in terms of different regulations including NIST 800-53, NIST 800-171, NIST CSF, ISO27001, PCI-DSS, OTA, HIPAA and GDPR. This process could be a vendor assessment in the due diligence process or a third party in an existing supply-chain.
This prediction is not a replacement for a regular compliance assessment, but it is a very good baseline to start working with. NormShield’s shared responsibility platform also allows users to update the compliance level of their organization after the estimated level by filling out questionnaires embedded in the platform. It can be thought of as a survey sent out to the vendor in the due-diligence process as complementary information to their Cyber Rating.
Learn more about the NormShield platform and grading
[1] Cost of a Data Breach 2020, https://www.ibm.com/security/digital-assets/cost-data-breach-report/#/
[2] https://www.nist.gov/cyberframework/online-learning/five-functions