According to CISOs interviewed at the 2020 RSA Conference, supply chain attacks are the most dangerous threats following ransomware. IBM Security’s recent report [1] emphasizes third-party involvement (a.k.a supply chain) as an amplifying factor to the overall cost of a breach, increasing the dollar amount by more than $200,000.

Let’s admit, supply chain security is not on the forefront of IT Security Professionals’ list. When companies think about security, they often think of securing their networks, software, and digital assets against cyber attacks and data breaches.
In the last blog we delved into definitions of supply chain. Here, let’s start from the ground up and cover some very basic questions surrounding supply chain security.
Q1: WHY DOES SUPPLY-CHAIN SECURITY MATTER IN THE FIRST PLACE?
Knowing why it matters is the key to start an effective supply-chain security program. It drives you to find the right parameters to input into your program as well as key decision metrics.
Supply-chain security matters because of the data and trending incidents against supply chain attacks. And – this trend isn’t new by any means. It is not the company itself that hackers often target, but weaker vendors in a supply chain. Take the Target breach which compromised 110 million customers’ data due to a third-party HVAC vendor. The data breach eventually cost Target $18.5M as a result of class-action settlements and victim expenses.
A more recent breach, the Blackbaud breach, affected dozens of beneficiaries including healthcare organizations and universities. These institutions are now sending their patients letters of breach notification.
Q2: WHAT IS MY COMPANY’S ROLE IN THE SUPPLY CHAIN?
Supply chains are evolving to be as much about the flow of information as they are about the flow of goods and services. Your company could be at the heart, or some other company that you provide services to along with many suppliers.
No matter what your place is in the whole ecosystem, Supply-Chain Security is every company’s responsibility. An attack towards a supplier in the chain affects your company along with many other vendors, as information flows in both directions. Therefore, it comes as no surprise that Supply-Chain Security is a highly complex and evolving function as digital assets are now closely intertwined in the cyber landscape.
Q3: WHICH DEPARTMENT IS RESPONSIBLE FOR SUPPLY-CHAIN SECURITY?
Toughest question of all. For most companies, there is no mature TPRM (Third-Party Risk Management) or SCRM (Supply Chain Risk Management) program in place. They all try to handle risk through a joint effort in the IT Security and Procurement department. The best way to start is perhaps setting up a division under the Risk Management department and have close relationships with IT, Procurement and Business Relationship departments.
Above all, the management must take ownership of Supply Chain Security and communicate the level of ambition for responsible supply chain management activities to all employees. This will help make supply chain management responsible and an integral part of the business strategy of the company. It will also make economic advantages visible to the organization.
At the end of the day, business continuity of the supply chain boils down to effectively assessing and managing risk through integration of necessary parties.
Q4: WHAT SHOULD MY ATTITUDE BE TOWARDS SUPPLY CHAIN SECURITY?
Everything starts with the attitude!
To start, companies must change the way they view security. It’s not just about securing your network, software, and digital assets against cyber attacks and data breaches. It is now about your vendors’ network, the software they provide to you and the assets you share with them as well as yours. Also, security is not a point-in-time configuration but an ongoing effort for the entire supply chain. We must accept that it is continuously changing and evolving, and take our guards accordingly!
“The big trend is people are looking at their supply chain. Like, what is the risk to the third parties you’re partnering with, to the code you’re developing with partners, so I think it’s about looking beyond that first circle to the second circle of your supply chain and your business partners.”
Akamai CTO Patrick Sullivan at RSA Conference
Q5: HOW DO I CLASSIFY MY VENDORS?
Classifying vendors in a supply chain is actually a more straightforward task than you might think. It could be an ecosystem of suppliers such as:
- Information Services
- Training Services
- Software Services
- Logistic Services
- Management & Support
- Hosting Services
Or could be the number of assets shared with the third party and status of internal access. One could organize its vendors based on the criticality and the volume of assets shared with that vendor. There are numerous cases in the data breach history validating this logic. Today, most of the Data Protection Authorities impose fines based on the number of personal records compromised and the sensitivity of these records. British Airways and AMCA breaches are good examples for demonstrating how the fines could go up depending on these factors.
Q6: HOW TO RATE SUPPLY CHAIN RISKS?
Supply chain risks are numerous, ranging from cybersecurity risks to manufacturing risks. As stated earlier, the continuity of a supply-chain is very much related to effectively assessing and managing risk. It is important that supply chain managers adopt a risk-aware attitude in the entire supply chain, whether it is a manufacturing risk or a security related risk. This logic, regardless of the domain, will allow them to focus their limited resources on suppliers/vendors who present a risk beyond the organization’s risk appetite, instead of performing time-consuming assessments on a vendor who poses a low probability of financial loss.
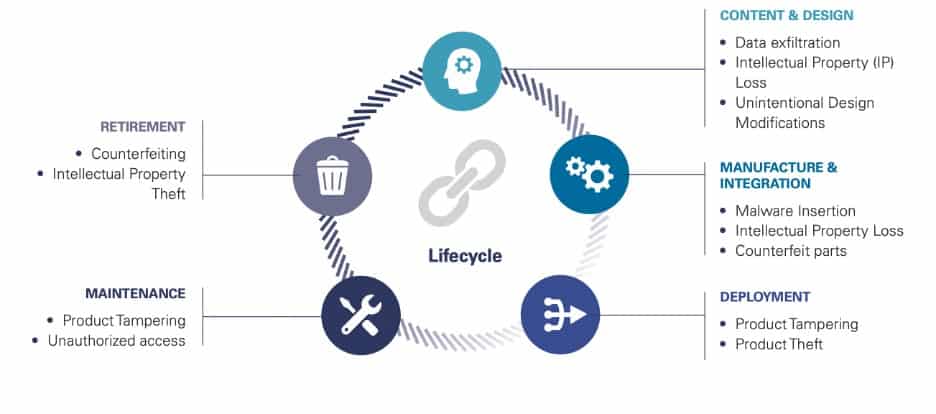 Source: [2]
Source: [2]
As in any risk management process, risk managers should start by having a good knowledge on information flow. It is important to know where your data stays in the entire supply chain. This will eventually lead you to the critical assets.
Assets can be anything, PII (names, email addresses, credentials, purchase info), servers, software, contracts, company proprietary information, e.g. manufacturing process, patented technique, essentially anything related to goods and services in the supply chain.
Threat scenarios on these assets and their possible consequences with regards to the contracts and regulations should also be thoroughly analyzed. Finally you should come up with a risk for each vendor in the supply-chain.
This is not a one-time event, since supply chains and the landscape they are dwelling in are continuously evolving.
“Supply chains need to be assessed and be continuously monitored with regards to their commitment to business’ risk tolerance, regulatory compliance and contractual requirements.”
Q7: WHAT DO BEST-PRACTICES SAY ABOUT SUPPLY-CHAIN SECURITY?
There are many standards, best practices and regulations out there, which outlines the relationships with suppliers. Each framework has its own say, most of the time focusing on sector-specific concerns. There are also commonalities among these frameworks; so below items could be taken as a general framework for supply-chain security:
- Adopt a Supply-Chain Risk Management program
- Audit your third parties or suppliers routinely to confirm they are meeting contractual obligations
- Consider each party / vendor and their obligations including the agreements.
For a detailed view of different standards , refer to NormShield’s Third-Party Risk in Standards and Regulations Report
Q8: IS THERE AN EFFECTIVE TOOL FOR MONITORING SUPPLY-CHAIN SECURITY?
Along with the best practices and frameworks, there are many tools out there, but note that one compliments another. Frameworks are good for providing a mind-set. It is up to individuals’ skills and efforts as well as to their previous experience to put a framework in place towards achieving a supply-chain security program.
Here is where the tools come into picture. Tools save you from manual effort. In the previous questions, we talked about how security is not a point-in-time configuration but an ongoing effort for the entire supply chain. Tools provide the automation of managing the security of complex and ever-evolving supply chains.
It could be a vulnerability assessment tool, or an SRS (Security Rating Service) or even a GRC tool (Governance, Risk , Compliance) integrated with other tools, but should provide the trending Security Performance of the supplier over time.
IBM Security’s Cost of a Data Breach Report 2020, points to the effect of security automation on cost of a data breach.
“The impact of security automation on data breach costs has grown over the past three years ”
Cost of a Data Breach Report, 2020, IBM Security & Ponemon Institute
According to the report, average cost savings of fully deployed security automation vs. no security automation is as high as $3.58M.
Q9: HOW DO I MAKE THE BEST OF NORMSHIELD’S CYBER RATING AND COMPLIANCE RATING IN MY SUPPLY CHAIN?
 NormShield’s Third-Party Risk Assessment continuously assesses an entity or a supplier throughout the entire supply chain, capturing critical information in the cyber risk dashboard and providing detailed drill-down capabilities to fully understand and mitigate the risk. Ongoing monitoring surfaces prioritize risks and measures cyber risk posture improvement over time.
NormShield’s Third-Party Risk Assessment continuously assesses an entity or a supplier throughout the entire supply chain, capturing critical information in the cyber risk dashboard and providing detailed drill-down capabilities to fully understand and mitigate the risk. Ongoing monitoring surfaces prioritize risks and measures cyber risk posture improvement over time.
NormShield utilizes 450 controls, of which 250+ are unique to a company’s cyber hygiene. The controls are broken down into 20 categories, each corresponding unique grades on vendor’s security posture in the entire supply chain as well as overseeing the average score of a supply chain.
NormShield correlates cyber risk findings to industry standards and best practices in the Compliance Module. The classification allows organizations to measure the compliance level of any vendor in your supply chain for different regulations and standards including NIST 800-53, ISO27001, PCI-DSS, HIPAA, GDPR, and Shared Assessments.
Q10: WHAT IS THE ROLE OF A FINANCIAL IMPACT RATING IN SUPPLIER RELATIONSHIPS?
Most of the supply-chain related security issues get “lost in translation” when reported upwards to the executive-level. NormShield uses the Open FAIR™ model to calculate the probable financial impact to estimate the potential loss should a breach occur in a supply chain.
Let’s say a supplier bears an annual risk of $195,000 according to Open FAIR. This is either beyond your company’s risk threshold and/or much higher than the business profit you are about to make with that supplier once the business deal is made. In this case, you can either hand out the supplier his/her Cyber Rating along with the technical report and ask him/her to fix the issues, or stop doing business altogether.
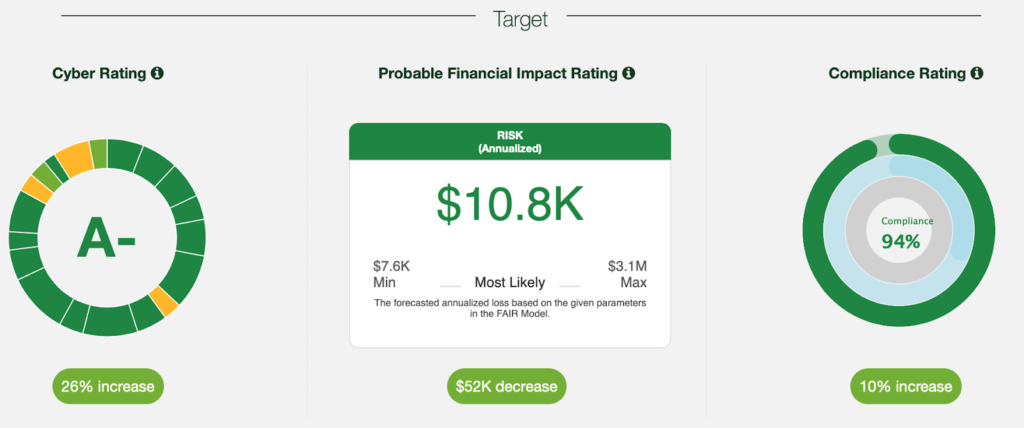
Having the capacity to use a FAIR assessment for supply chain risk management elevates the risk management program. This tool helps attain the goal of cost-effectively achieving and maintaining an acceptable level of loss exposure.
Open FAIR™ is the only international standard Value at Risk (VaR) model for cybersecurity and operational risk. Platform users can leverage Open FAIR™ results in prioritization of resource allocation.
By providing a Cyber Rating (technical), Compliance Estimations (policies and processes) and FAIR results (the probable impact in financial numbers), NormShield provides a 3-dimensional risk picture of a supply chain.
You’re Only As Strong As Your Weakest Link
There’s never a more vital time to start thinking seriously about the security posture of your organisation and the cyber supply chain you rely on. As an authorised NormShield Managed Service Partner, DVV Solutions are here to help with a range of services and solutions proven to improve your ability to assess, analyse and manage more Third-Party cyber and data privacy risk domains. For more advice and information on any Third-Party risk challenge you have:
Call Us: +44 (0) 161 476 8700
Contact Us: Complete our Contact Form, or
Learn more about What We Do
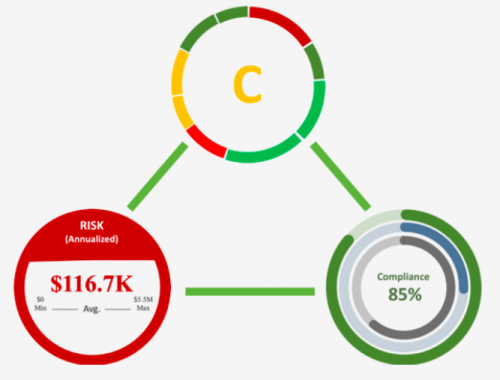 NormShield Cyber Risk Ratings
NormShield Cyber Risk Ratings
Monitoring and continuous oversight on your cybersecurity posture and that of your Third-Party vendors and supply-chain are critical. That goes beyond your organisation including anywhere your data is handled during the process.
NormShield Cyber Risk Ratings and Assessments continuously assesses an organisation, captures critical information in the cyber risk dashboard and provides detailed drill-down capabilities to fully understand each risk. Ongoing monitoring surfaces priority risks and measures cyber risk posture improvement over time.
By providing Cyber Rating (technical), Compliance Estimations (policies and processes) and FAIR results (the probable impact in financial numbers), NormShield’s vision is to give a complete risk picture.
Request your Free Rapid Cyber Security Rating here.
This article was originally published by NormShield Cybersecurity and is shared with their kind permission.
References:
[1] https://www.ibm.com/security/data-breach
[2] https://www.dni.gov/index.php/ncsc-what-we-do/ncsc-supply-chain-threats