 Part 4: “Treating Third Parties as
Part 4: “Treating Third Parties as
Trusted & Valued Partners”
This TPRM blog series, compiled by experienced CSO, Bob Maley of NormShield Cybersecurity, has been designed to help CISOs and other risk management practitioners examine their programs from a unique perspective – one in which the objective problem your organisation is trying to solve takes center stage and risk managers can effectively respond as that problem morphs over time.
This is the final part of a four part series. You can catch up with the series via the links below:
2) Understanding and Quantifying the conditions that create third party risk, or
3) Strengthening your Strategy
Executing your plans for assessments:
The most important thing for practitioners to bear in mind is that there are parties outside your TPRM program that must be engaged, in order for your program to run effectively. Focus your effort on those parties, both internal to your organisation and external third party partners, that matter to your business.
It’s that simple – and it’s that complicated.
The point here is that when expectations are clearly laid out in the planning stages:
– Your TPRM strategies and tactics can yield results that are in keeping with your needs.
– Your approach will be appropriate to the scale of the resources your company wishes to invest in controls assessment and relationship management.
Keeping optimisation in focus:
In Part 2 of this series, we discussed the need to focus TPRM program resources in accord with the potential impact that is posed by third parties with network access, access to sensitive data, and those that hold critical roles for your business.
To do so, your TPRM program’s processes will need to reveal insight into your vendor’s risk management maturity, centering on your vendor’s own risk management processes. What about that third party is most important for your relationship? Both trust (vendor self-assessments) and verify (independent assessments) should reveal relevant information about the vendor’s ability to execute for your company, their motivations, and how those two factors affect their own risk management priorities. For instance: do they have a risk evaluation process; do they perform a root analysis process; what are their patching and maintenance processes; do they have an asset inventory; do they have a management process for controls and reviews, etc.? If they are doing these things in a way that is responsive to your needs, that is a good indicator the vendor has a more advanced level of risk management maturity.
You will also need an outside view of the vendor. This can be accomplished in number of ways, such as using open source intelligence tools in a do-it-yourself manner, engaging a third party monitoring vendor to perform this task for you, or combining the two approaches. If a monitoring vendor is used to collect information on your third parties, that vendor will apply rules and often its own proprietary behind-the-scenes algorithms to make it easier for its customers to consume that information, usually providing dashboard output in the form of a graded score (by color, rank, etc.) for each vendor.
Understanding HOW the score is created.
That’s how you make better business decisions:
Remember that there are no ‘magic bullets’ in TPRM – no one service can cover all the bases. When you go to an outside source for intel (OSINT), there are cues that can help guide you in selecting a monitoring services vendor. Red flags when you review automated monitoring services is any marketing material that claims:
1) the vendor can completely replace assessments (i.e., their service is “all you need”);
2) that the vendor provides ‘actionable’ intelligence, or;
3) that the vendor can radically reduce the amount of time and effort you need to apply in your TPRM program and processes.
All these claims should make your ‘Spidey’ senses tingle.
For example, let’s talk about actionable intelligence. In TPRM, intelligence is the term used to define the information gathered through collection efforts to gain details about a vendor’s risk posture. Actionable intelligence is a subset of that information. In military terms, actionable intelligence is: “intelligence information that is directly useful to customers for immediate exploitation without having to go through the full intelligence production process.”[1]
While scored information and dashboards can make the information collected more valuable, it doesn’t necessarily make the information “actionable”.
Information becomes actionable when the end user of that information (i.e., you, the outsourcer) go through the Observe and Orient steps of the OODA (Observe-Orient-Decide-Act) Loop.
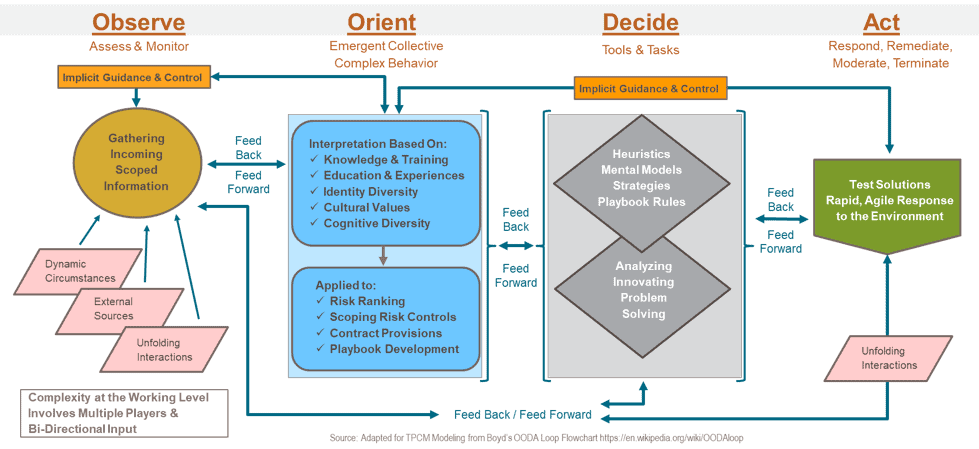 Figure: The Parts of the OODA Loop [2]
Figure: The Parts of the OODA Loop [2]
The vendor providing the intelligence may do some Orientation on the larger body of information (either through a transparent, known process, or through an unknown black box manipulation). When the vendor passes that manipulated intel to you, it is up to you as the TPRM practitioner to further Orient that information and Decide to Act in the context of what action would be best aligned with your company’s TPRM program’s goals and objectives. Only if you accept the monitoring vendor’s intel as it comes to you – without any further alignment to your program’s needs – can the monitoring vendor’s reported information be truly termed “actionable.”
If your TPRM program is so new that you cannot align the incoming intel to your own company’s risk appetite, and you make the business decision to use the monitoring vendor’s raw intel as is, then (and only then), acting on that data is a valid decision. HOWEVER, if you do use that data and act upon it, you must understand HOW the graded score is created, because if you Act without further analysis, that will have an impact to your company and your relationship with your third party. The lack of analysis on your part will also cause churn for you, since the undigested nature of the intelligence provided means it will be, by definition, less tightly focused on your program’s needs.
The bottom line is that you are responsible for how that intel is used. If you are assessing one of your preferred vendors and you recommend a specific action about that third party based on intelligence that has not been well-aligned to your company’s needs, then your tenure as a TPRM practitioner may be quite short.
Staying focused:
To make sure you are focusing on the right vendors; an up-to-date and extremely precise and accurate vendor inventory is required. That inventory should provide insight into who in your company owns each vendor relationship, the criticality of that vendor to your operations (including concentration risk), if and how the vendor is connected to your network, and the type and sensitivity of the data they have access to (including intellectual property, operations technology, and customer data). In addition to helping to guide procurement and onboarding, as well as regular assessments, this inventory provides essential information both before and after any incident, ensuring that the right people are involved throughout the vendor lifecycle.
As discussed in Part 3 of this series, when conducting assessments and monitoring activities, restrict your questions to those things that really matter to you. You should include inherent, target, and residual risk, to keep your program focused, so that you don’t waste your own or your third party’s resources.
Part 1 demonstrated the importance of getting as much of your third party ecosystem under your control as possible. In other words, don’t focus on EVERY third party. Focus first on those that are critical to your operations and have network and data access (or potential access) – remember that a seemingly benign third party can serve as a gateway for hackers trying to gain network access, as noted in Part 2. Where vendors connect to your network, strong network segmentation is a key requirement for controlling risks. Try to work with your technology groups to make sure that you have control of as much of those third parties’ access to information and the network as possible.
Using contracts to set expectations:
A key component for optimising your third party relationships is very clear contractual language. The language will depend on the type of service that the vendor is performing. You can develop your own standard, pre-approved templates to minimise your need for legal to be involved in initial negotiations. There should also be language that sets out the expectation that vendors will follow industry standard information security framework(s).
If your vendor is handling payment processing, for instance, that vendor would need to meet the scope of Payment Card Industry Data Security Standard (PCI DSS) requirements. Therefore, you would include requirements in your contract that cover those standards setting the expectation that the vendor would be and remain compliant and report appropriate around PCI DSS. Fourth party requirements should also be called out in specific clauses (such as, if and when the use of fourth parties is permissible, under what circumstances they may be used, and the requirement for the third and fourth party risk management processes to meet or exceed your own company’s risk management requirements).
The Shared Assessments Program’s Principles of Third Party Contract Development, Adherence & Management and its companion Executive Summary document provide guidance on contract development practices that provide benefits to both the outsourcer and the third party provider.
Treating third parties as trusted and valued partners: Plan for success in ways that help your third parties to improve their own risk management programs and everyone comes out stronger. Treat your third party’s as valued partners, rather than liabilities. Bear in mind that you are not the only company to which they provide services. Don’t waste their time with unfocused questionnaires and other assessments. When an item is identified that requires remediation to meet your control requirements, provide the vendor with not only a statement of what the problem is, but also how it matters to you and how they can easily resolve the problem to meet your needs. This helps your vendors to elevate their security maturity, instead of overwhelming them with meaningless issues.
Some companies handle this aspect of relationship management far better than others. In many cases, outsourcers monitoring includes conducting vulnerability management scans and simply handing off a report to the IT department that is running the scanned server without providing any focused feedback. The vulnerability report may cover thousands of issues and simply telling your vendor that all issues must be immediately fixed is not a recipe for success. In most cases, a targeted remediation request will resolve the important issues. Go with what’s important.
Recommendations:
Finally, remember that building a TPRM program is a long-term improvement cycle process. The use of the OODA Loop, not just to manage the information around your third parties, but also for the improvement to your TPRM program is mission critical. Research your metrics to make sure they will provide useful information instead of churn.
Set out clear expectations that matter. Don’t waste time. So that all parties involved are making better use of existing resources, concentrate program design and implementation efforts by acutely focusing on the most vulnerable, high risk vendors in your processes.
Understanding where you are today, the improvements you make tomorrow, and knowing what your ultimate goal is for program maturity – all of these are key to success. The Shared Assessments Program has honed a valuable, freely available tool that all companies can and should use to benchmark their program maturity. The Vendor Risk Management Maturity Model (VRMMM) Tool, helps TPRM practitioners at all levels of goal setting, program development, and continuous program improvement.
About the Author
Bob Maley, CTPRP, CRISC Chief Security Officer, NormShield Cybersecurity is an award winning senior leader in information security and a strategic thinker with experience as an information security strategist designing and building information security programs for PayPal Holdings, the Commonwealth of Pennsylvania, and for the healthcare sector.
[1] Publication JP 2-01.2. Joint and National Intelligence Support to Military Operations. July 5, 2017.
[2] Innovations in Third Party Continuous Monitoring: With a Name Like OODA, How Hard Can It Be? The Santa Fe Group, Shared Assessments Program. 2018. Reprinted with Permission.